Strategize and Range WITh Proven IT Managed Solutions Techniques
In the fast-paced landscape of contemporary company, the strategic application of IT handled services has actually ended up being a cornerstone for organizations aiming to boost operational performance and drive sustainable development. By carrying out proven approaches tailored to meet certain business demands, companies can browse the complexities of technology while remaining active and affordable in their respective sectors. As the demand for scalable IT remedies remains to rise, comprehending how to properly strategize and take advantage of managed services has never ever been more vital. It is within this world of innovation and optimization that services can truly unlock their prospective and lead the way for future success.
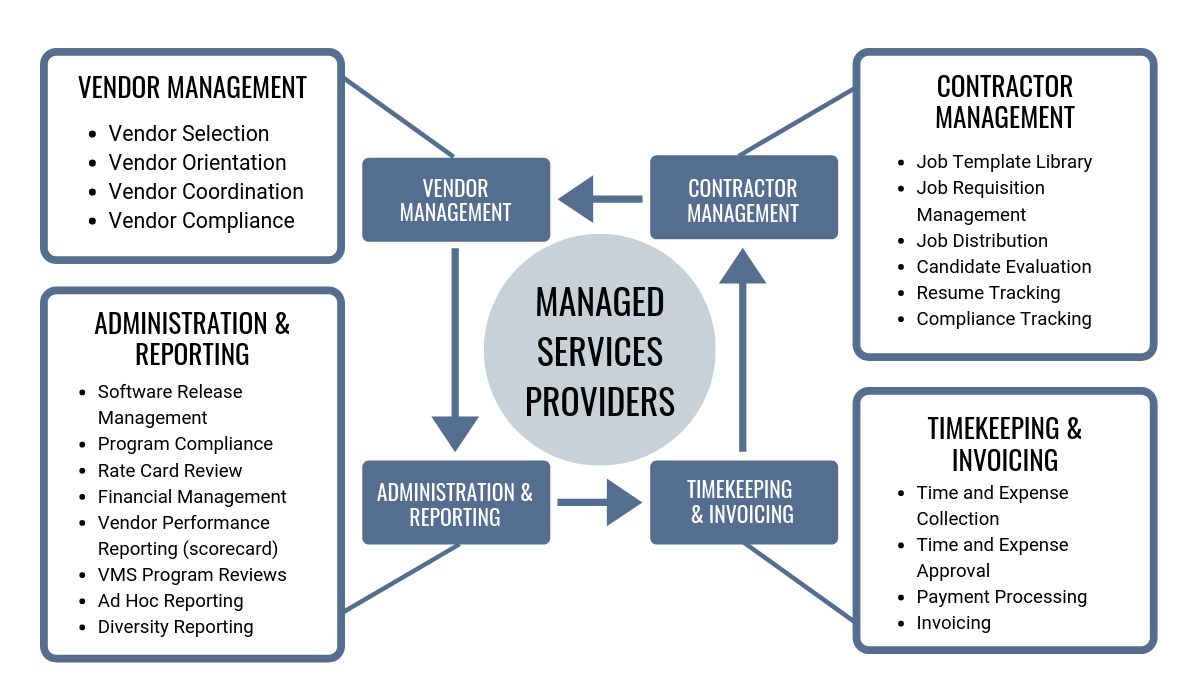
Advantages of IT Handled Provider
Undoubtedly, the advantages of IT Managed Providers are paramount in enhancing business performance and decreasing downtime. By outsourcing IT monitoring to a specialized company, services can touch into a riches of expertise and resources that would or else be pricey to keep internal. Among the key advantages of IT Managed Services is proactive surveillance and upkeep of systems, which aids stop potential problems before they escalate right into significant issues. This positive approach translates into enhanced system uptime, decreased downtime, and enhanced total performance for the organization.
This ensures that companies continue to be competitive in a rapidly progressing technological landscape. In conclusion, the advantages of IT Managed Solutions are instrumental in enhancing procedures, improving performance, and ultimately, driving organization success.
Trick Methods for Application
With an understanding of the substantial advantages that IT Managed Solutions offer, services can now concentrate on applying vital techniques to successfully integrate these solutions right into their procedures. One crucial strategy is to clearly specify the scope of services called for. This involves performing an extensive evaluation of existing IT infrastructure, identifying discomfort factors, and setting particular goals for improvement. Additionally, businesses must establish clear interaction networks with their taken care of company to guarantee smooth partnership and timely issue resolution.
An additional important strategy is to focus on cybersecurity steps. Data violations and cyber threats posture considerable threats to services, making protection a leading concern. Carrying out robust safety protocols, regular surveillance, and timely updates are crucial actions in safeguarding sensitive details and preserving organization continuity.
Moreover, businesses need to establish service degree agreements (SLAs) with their handled company to specify expectations, duties, and efficiency metrics. SLAs aid in establishing clear guidelines, ensuring accountability, and preserving solution top quality standards. By integrating these key approaches, organizations can take advantage of IT Managed Solutions to enhance operations, boost efficiency, and drive lasting growth.
Maximizing Effectiveness Through Automation
In addition, automation enables real-time tracking and information analysis, providing valuable understandings for informed decision-making. By automating routine tracking tasks, companies can proactively deal with issues before they rise, lessening downtime and enhancing efficiency (Managed Service Providers near me). Additionally, automation can help with the smooth integration of different systems and applications, enhancing collaboration and data circulation across the organization
Ensuring Data Protection and Conformity
Data security and conformity are extremely important worries for businesses running in the electronic landscape these days. With the raising volume of delicate data being saved and refined, guaranteeing durable safety measures is vital to protect against cyber dangers and abide by regulative needs. Applying extensive data protection techniques involves encrypting information, developing access controls, on a regular basis upgrading software program, and carrying out protection audits. Conforming with policies such as GDPR, HIPAA, or PCI DSS is vital to maintain and stay clear of expensive charges trust with consumers. Handled IT companies play an important role in aiding services navigate the facility landscape of information safety and security and compliance. They supply proficiency in applying safety methods, checking systems for prospective breaches, and guaranteeing adherence to industry regulations. By partnering with a trustworthy took care of companies, businesses can enhance their information safety and security position, alleviate risks, and show a commitment to safeguarding the confidentiality and stability of their data possessions.
Scaling IT Framework for Growth
Incorporating scalable IT framework options is vital for facilitating organization growth and operational efficiency. As companies expand, their IT requires advance, requiring infrastructure that can adjust to raised demands effortlessly. By scaling IT framework effectively, organizations can make certain that their systems remain check this trusted, safe, and performant also as workloads expand.
One trick element of scaling IT facilities for growth is the capacity to flexibly designate sources based on present needs. Cloud computer solutions, for instance, offer scalability by allowing businesses to adjust storage, refining power, and various other resources as needed. This elasticity enables firms to effectively take care of spikes in need without over-provisioning sources during periods of lower task.
Moreover, applying virtualization technologies can improve scalability by enabling the development of virtual circumstances that can be easily duplicated or customized to accommodate altering workloads - it managed service providers. By virtualizing web servers, storage space, and networks, companies can enhance resource use and simplify IT management processes, eventually supporting business growth initiatives successfully
Conclusion
In conclusion, applying IT took care of solutions can bring various benefits to a company, such as enhanced performance, improved data safety and security, and scalability for growth. By adhering to crucial strategies for implementation, utilizing automation to make best use of performance, and guaranteeing information protection and conformity, companies can better plan and scale their IT framework. It is vital for companies to develop and adapt with technical improvements to stay affordable in today's ever-changing landscape.